December is upon us, so my wife and I have started our annual Christmas movie binge. I finished this script up while we had Die Hard on, and kept wandering back into the study to check my desktop’s ARP cache as the book suggested.
I’ve done my usual thing of adding an argument parser to it, and I’ve made a couple of hacks to try and make everything shutdown a little more cleanly.
The way it works
The scripts are starting to get a little more interesting in the book now. This feels like something a little more practical to play with, and it could potentially use this as a MITM if you captured the packets and monkied with them.
Like the book explains, we craft a link layer packet and send it on the wire. The packet will contain
- A sender hardware address
- A sender IP address
- A target hardware address
- A target IP address
I ran wireshark to capture some of the packets and see how it all worked
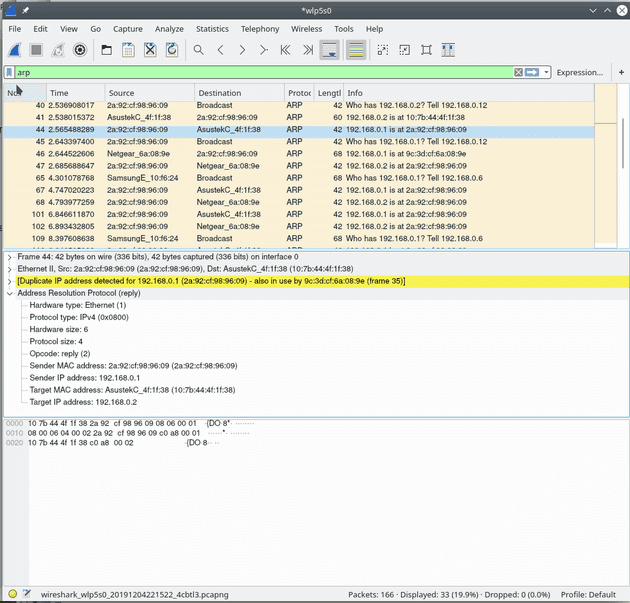 This builds up an ARP cache on the target machine, which can be viewed
using the
This builds up an ARP cache on the target machine, which can be viewed
using the arp command. I ran this against my Windows desktop and was able
to successfully set my Arch laptop as its gateway. Good fun.
Interesting notes
Check out the wireshark screengrab above. Apparently Samsung TVs ask for their gateway’s MAC address every two seconds or so. Very interesting.
Also of note is that I’ve come to hate exceptions in Python. Having been using golang for the last little while I love returned errors and think it’s probably the best way to do it, simple and elegant. The Python way of handling interrupts and exceptions seems entirely random, maybe I need to do some more reading about it to figure it out.