So with the last blog I published, my build failed and I didn’t realise for a day or two. Not being happy with that situation, I turned to one of the things I learned in my preparation for the devops pro certification.
How this Blog Works
For some extra context, this whole site uses Gatsby to build static HTML. On the AWS side, it’s served off a private S3 bucket with a CloudFront distribution in front of it, and I use CodePipeline to build and deploy it out when I commit and push a new markdown blog post.
CodePipeline
CodePipeline is a build tool that tries to take away a lot of the pain from manual builds and deployments. It has tight integration with CodeCommit, CodeBuild and CodeDeploy and can run those tasks with minimal configurations for projects like mine.
Other tight integrations it provides is with CloudWatch and SNS, which are what we’re going to use here for our notifications.
Setting Up Our SNS Topic
The first step is to create an SNS topic, which we can do easily from the AWS CLI tool:
$ aws sns create-topic --name gimme-alertsRunning this should give you a response like this:
{
"TopicArn": "arn:aws:sns:ap-southeast-2:123456789123:gimme-alerts"
}Next we’ll add our phone to it. You could also use an email address, HTTP/S endpoint, or a Lambda ARN if you wanted to.
$ aws sns subscribe --topic-arn arn:aws:sns:ap-southeast-2:123456789123:gimme-alerts --protocol sms \
--notification-endpoint "+61433333333"Which, if successful, will tell you something like this:
{
"SubscriptionArn": "arn:aws:sns:ap-southeast-2:123456789123:gimme-alerts:34f847d2-9e0b-4bb5-8089-25b2717ef3d8"
}Let’s also test it to make sure it works
$ aws sns publish --message "test" --topic-arn arn:aws:sns:ap-southeast-2:123456789123:gimme-alertsIf you don’t get your test text, you might also need to verify your phone number.
$ aws sns opt-in-phone-number --phone-number +61433333333
$ aws sns verify-sms-sandbox-phone-number --phone-number +61433333333 --one-time-password 9999Next step is to get CodePipeline sending its events to the topic
Configuring CodePipeline
CodePipeline can be set to notify an SNS queue when a few different things happen:
- A pipeline changes state
- A pipeline stage changes state
- An action within a stage changes state
- Manual intervention is required, fails or succeeds
We create our notification rule with a command such as the following:
$ aws codestar-notifications create-notification-rule \
--resource arn:aws:codepipeline:ap-southeast-2:123467789123:www.stephengream.com \
--targets TargetType=SNS,TargetAddress=arn:aws:sns:ap-southeast-2:123456789123:gimme-alerts \
--event-type-ids codepipeline-pipeline-pipeline-execution-started \
codepipeline-pipeline-pipeline-execution-failed \
codepipeline-pipeline-pipeline-execution-succeeded \
--name giving-alerts \
--detail-type BASICEvent type IDs are a bit difficult to track down, so here’s a list you can use here
codepipeline-pipeline-action-execution-succeededcodepipeline-pipeline-action-execution-failedcodepipeline-pipeline-stage-execution-startedcodepipeline-pipeline-pipeline-execution-failedcodepipeline-pipeline-manual-approval-failedcodepipeline-pipeline-pipeline-execution-canceledcodepipeline-pipeline-action-execution-canceledcodepipeline-pipeline-pipeline-execution-startedcodepipeline-pipeline-stage-execution-succeededcodepipeline-pipeline-manual-approval-neededcodepipeline-pipeline-stage-execution-resumedcodepipeline-pipeline-pipeline-execution-resumedcodepipeline-pipeline-stage-execution-canceledcodepipeline-pipeline-action-execution-startedcodepipeline-pipeline-manual-approval-succeededcodepipeline-pipeline-pipeline-execution-succeededcodepipeline-pipeline-stage-execution-failedcodepipeline-pipeline-pipeline-execution-superseded
Testing it Out
Let’s start our pipeline and see if we get that text:
$ aws codepipeline start-pipeline-execution --name www.stephengream.comIf this doesn’t send you a notification, it could be that your pipeline’s IAM execution role doesn’t have the required permissions to publish messages to the topic. Make sure your pipeline can publish messages in both the IAM role and the SNS policy and give it another go. A telltale sign of this is the CodePipeline notification console showing “Unreachable” next to the SNS topic.
The SNS access policy will look like the following:
{
"Version": "2008-10-17",
"Id": "__default_policy_ID",
"Statement": [
{
"Sid": "StatusNotificationsPolicy",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789123:root",
"Service": "codestar-notifications.amazonaws.com"
},
"Action": "sns:Publish",
"Resource": "arn:aws:sns:ap-southeast-2:123456789123:gimme-alerts"
},
{
"Sid": "__default_statement_ID",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": [
"SNS:GetTopicAttributes",
"SNS:SetTopicAttributes",
"SNS:AddPermission",
"SNS:RemovePermission",
"SNS:DeleteTopic",
"SNS:Subscribe",
"SNS:ListSubscriptionsByTopic",
"SNS:Publish",
"SNS:Receive"
],
"Resource": "arn:aws:sns:ap-southeast-2:123456789123:gimme-alerts",
"Condition": {
"StringEquals": {
"AWS:SourceOwner": "123456789123"
}
}
}
]
}And you can update the policy with this command
$ aws sns set-topic-attributes --topic-arn arn:aws:sns:ap-southeast-2:123456789123:gimme-alerts \
--attribute-name Policy \
--attribute-value file://accesspolicy.jsonWhen you get a message, you should receive something like this
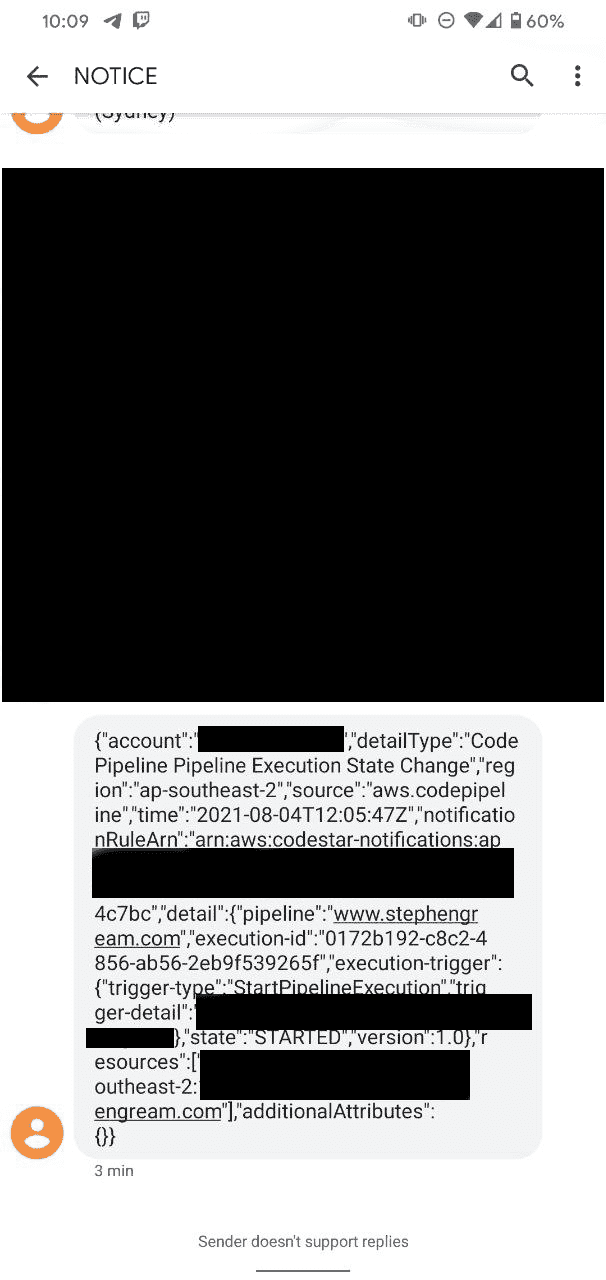 A big JSON blob. Hopefully this is enough of an example to get you started here, though, and start doing some
interesting things with your pipelines.
A big JSON blob. Hopefully this is enough of an example to get you started here, though, and start doing some
interesting things with your pipelines.
More Fun
The SNS messages here allow for more or less infinite possibilities of automation based on the build status at each point in the build and deploy process. I didn’t need anything too complex, so I’ve done something basic to serve my needs.
I’ve hooked this up to a Lambda which will push these alerts via Telegram, which you can find the code for on my Github. Check it out and send me some hatemail telling me it’s horrible.